Integrations
Table of contents
Summary
FIM supports integration with two platforms (one at the same time). The integration will help users to store in the cloud all the events produced by FIM in a easy way. The stored events could be processed and analyzed lately.
Supported integrations
FIM supports two integrations:
- ElasticSearch 8.x or OpenSearch 2.x
- Splunk indexer 9.x
ElasticSearch/OpenSearch integration configuration
The ELS/OS integration is set by the endpoint configuration section. This section has different options, but the required ones are the following:
- ElasticSearch/OpenSearch
address. This address has to be addressable by the FIM node. Theaddressusually includes the port that ELS/OS by default uses the 9200, an example of theaddressfield:https://elastic.example.com:9200.
Review the
insecureparameter in a testing environment. In the production environment, you should useinsecure: falseor keep it empty as defaultfalse.
- Inside the credentials section, it’s required to set the
userandpasswordparameters to access the indexer environment.- The
userparameter has to contain an ELS/OS username with permission to push an object into an index and create an index. - The
passwordparameter has to contain the access password of the previously given user.
- The
To see all endpoint parameters take a look at Configuration file
Those are all the required steps to start working with ElasticSearch or OpenSearch indexer tools. FIM will create the index of the day called fim-yyyy-mm-dd. Any produced event that FIM detects will be in this index.
Splunk integration configuration
The Splunk integration is set by the endpoint configuration section. This section has different options. In addition, the Splunk integration will require additional steps to receive FIM events into the Splunk indexer. The steps are the following:
First, it is required to configure the Splunk indexer to accept FIM events.
-
At the Splunk home page, click on the
Settingstab.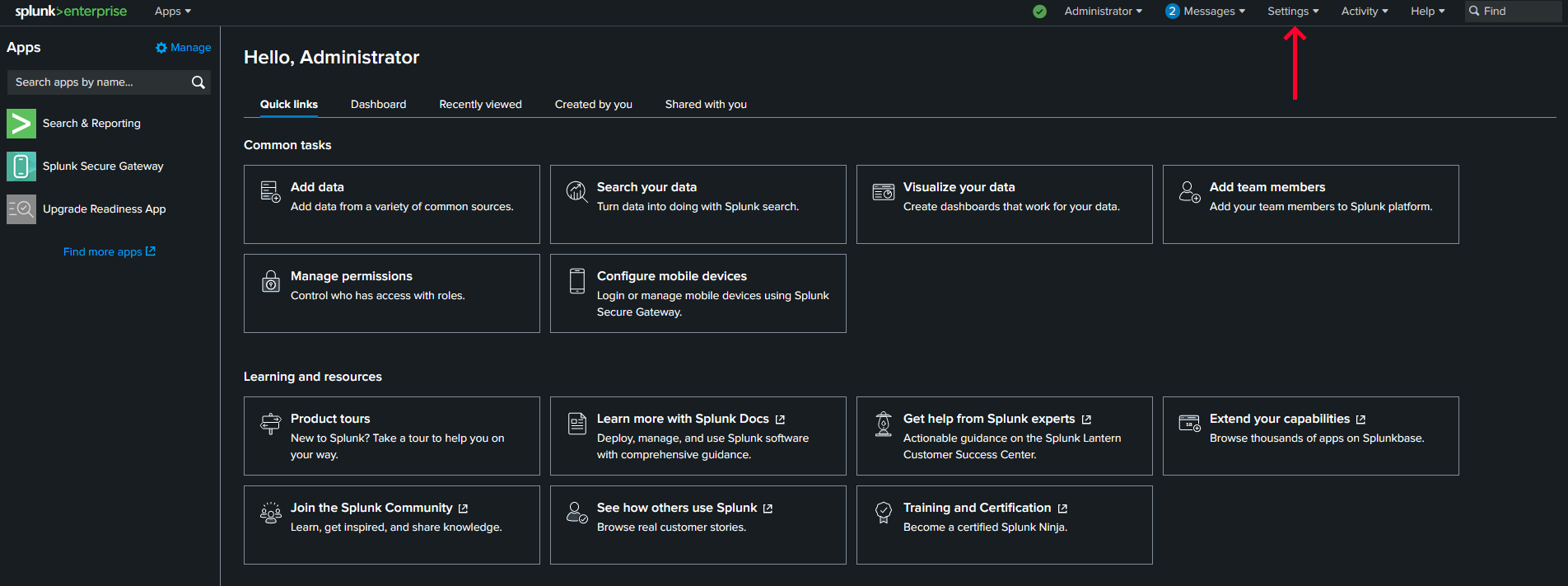
-
Select the
indexessetting inside the panel.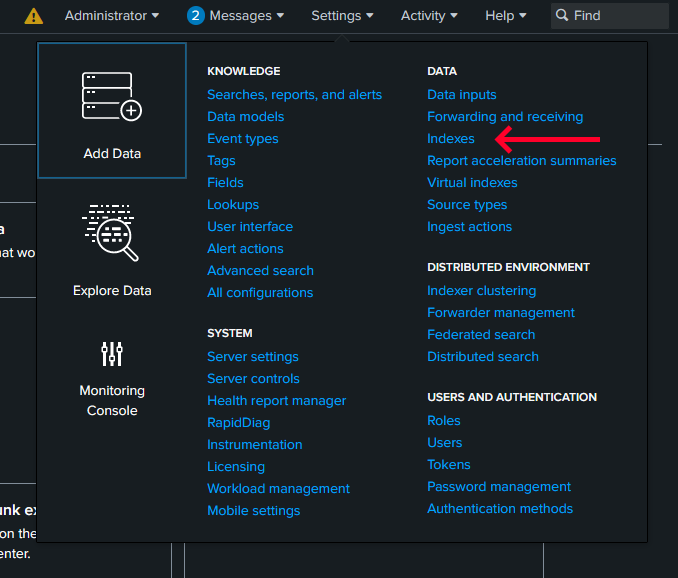
-
Click on the
New Indexbutton to create the FIM index.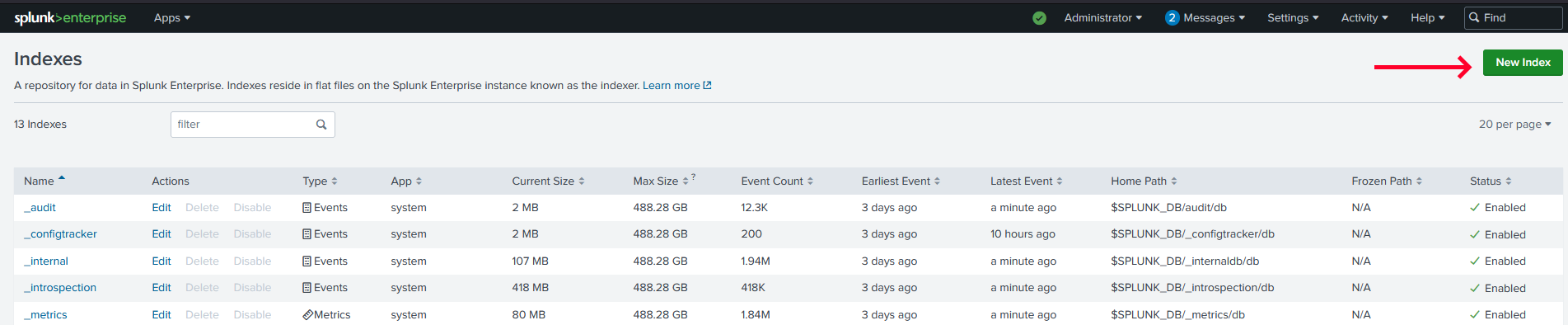
-
The name of the index must be
fim_eventsdo not change please, click onSave.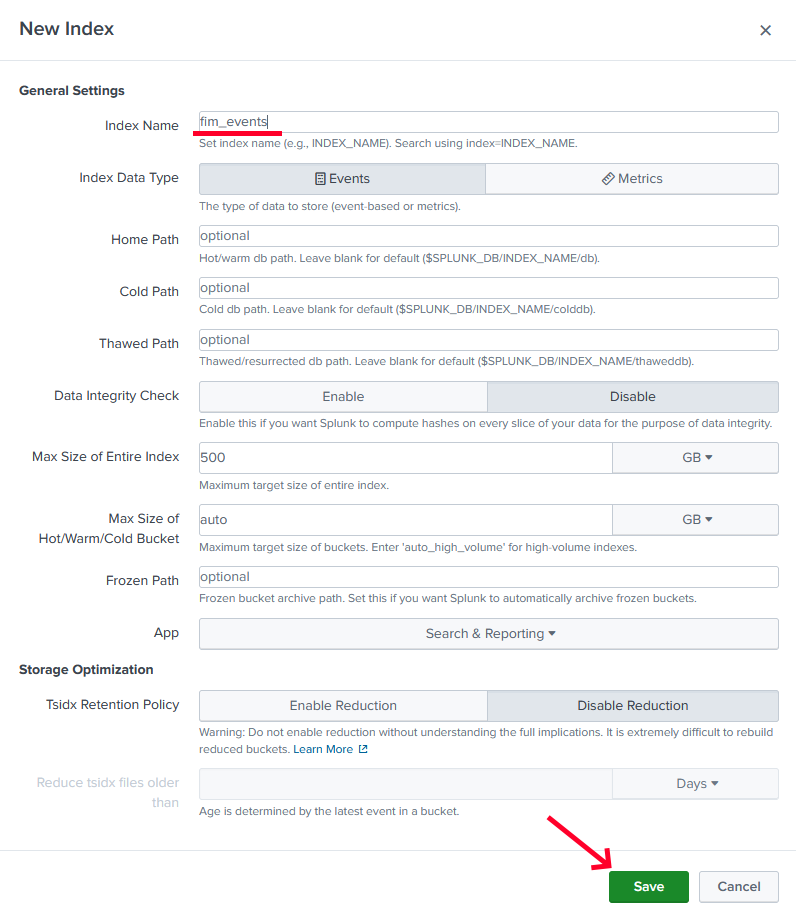
-
Go to the
Settingstab and click onData inputs.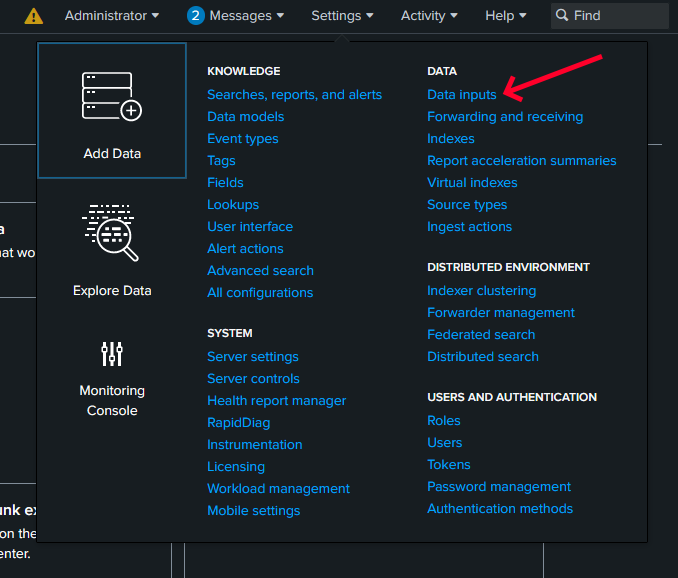
-
Click on
+ Add newto add a new HTTP Event Collector item.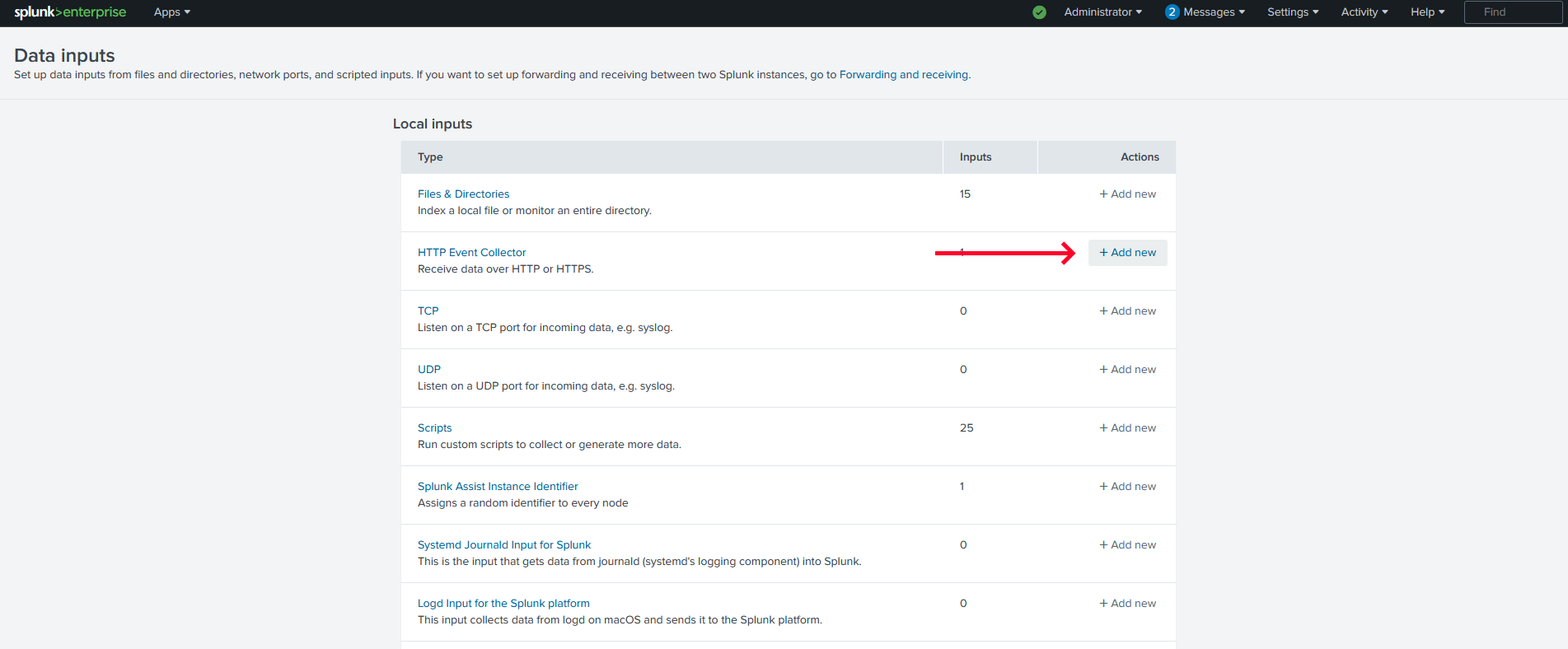
-
Set your HTTP Event Collector name as you wish, and click on
Next.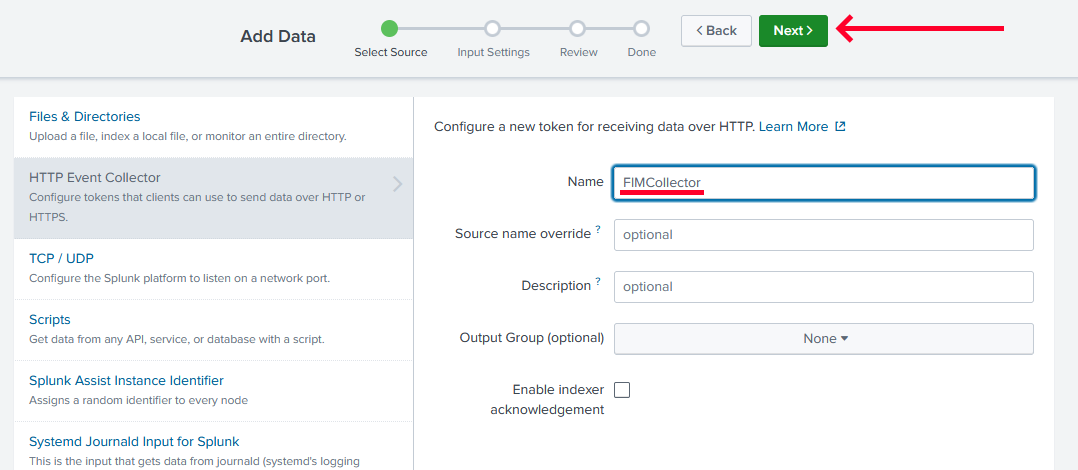
-
Give the collector permission to push into the
fim_eventsindex, set it as the default index, and click onReview.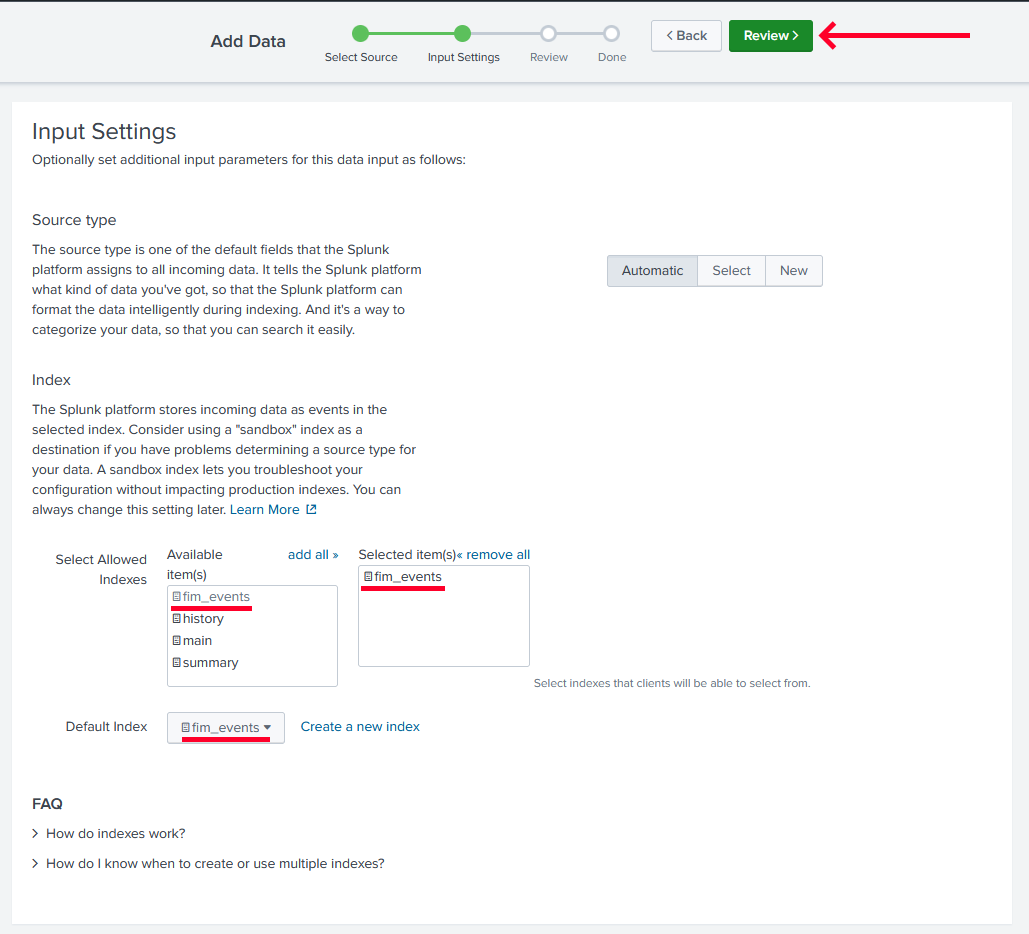
-
Review your configuration and click on
Submit.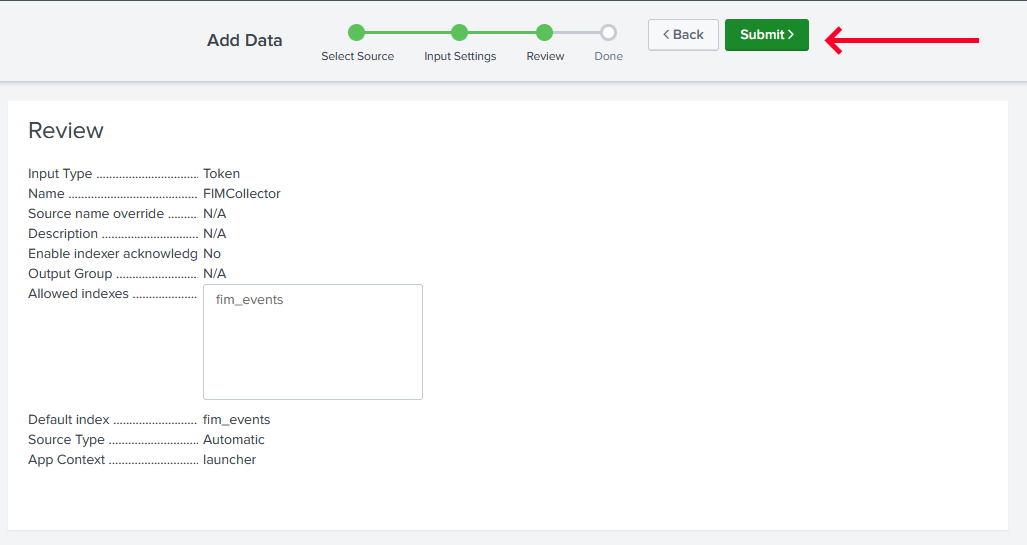
-
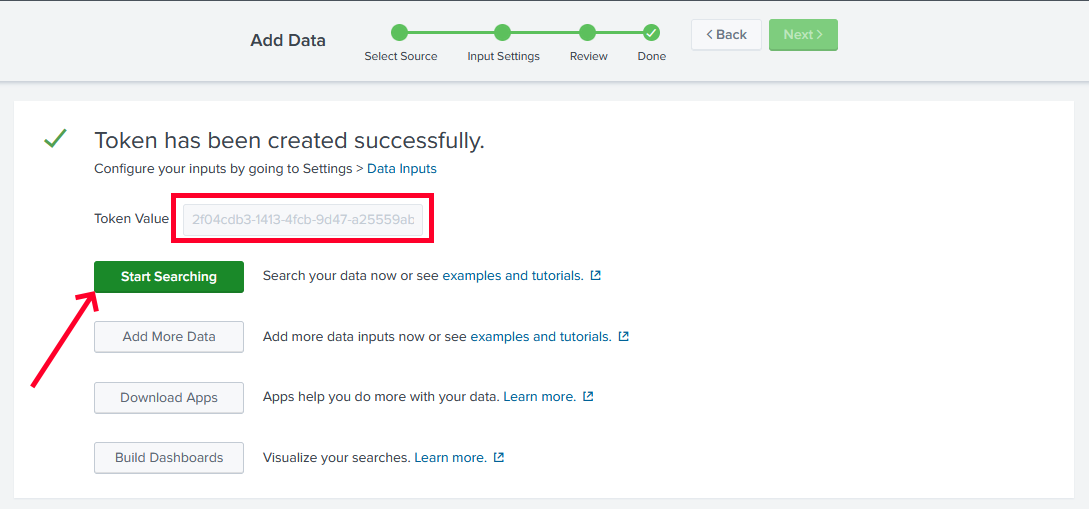
Splunk gives the token required in FIM configuration to push events into Splunk, copy the token and keep it secret.
-
Configure the endpoint address with the default HTTP event collector
8088and the token obtained in the previous step.
The HTTP Event Collector works by default in HTTPS mode. So, FIM needs to contain the
https://address in the configuration file.
Those are all the required steps to start working with Splunk indexer tools. Any produced event that FIM detects will be in this index.
